Upload of File Was Successful but Error Occurred While Setting the Permissions and/or Timestamp
If you want to lock user's they want to upload, download and edit files from a spider web root directory, and then that they cannot access folders outside from that, you can set upward a SFTP Chroot Environment on your Linux server.
For this post I will apply Ubuntu 20.04.iii LTS with OpenSSH version viii.2p1
OpenSSH supports since version 4.9p1 out of the box to fix a Chroot-Environment.
To decide the OpenSSH version on your server you lot tin use:
ssh -v localhost
Commencement we demand to configure SSH, then open up the /etc/ssh/sshd_config file. By default the subsystem SFTP part will looks similar this on Ubuntu.
# override default of no subsystems Subsystem sftp /usr/lib/openssh/sftp-server # Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server
To tell OpenSSH to lock user'south from a specific grouping, I volition create here a grouping named sftp, for which user's inside this group, should be locked aka chrooted to a specific folder.
So adjust the /etc/ssh/sshd_config file equally follows.
# override default of no subsystems #Subsystem sftp /usr/lib/openssh/sftp-server Subsystem sftp internal-sftp # Case of overriding settings on a per-user footing #Match User anoncvs Match Group sftp ChrootDirectory %h ForceCommand internal-sftp X11Forwarding no AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server
First I commented the line with the default subsystem libraries to avert the need for installing additional libraries (defended standalone sftp server).
OpenSSH: Difference between internal-sftp and sftp-server
Subsystem sftp /usr/lib/openssh/sftp-server
Subsystem sftp internal-sftpBoth sftp-server and internal-sftp are office of OpenSSH. The sftp-server is a standalone binary. The internal-sftp is simply a configuration keyword that tells sshd to utilize the SFTP server lawmaking built-into the sshd, instead of running another process (what would typically be the sftp-server).
The next ii lines with
Match Grouping sftp
ChrootDirectory %h
will force all user'due south from the sftp group to be locked (chrooted) to its own home directory.
The line
ForceCommand internal-sftp
will forcefulness OpenSSH again to use the internal sftp server code built-into sshd, instead of running another process similar the standalone sftp-server.
X11 Forwarding will back up to open graphical programs similar browsers, GUI text editors and more by using a SSH terminal like putty, for our case nosotros practice non need and want to enable them. Further downwards we also deny for the user in general to access a shell or terminal.
AllowTcpForwarding will allow you to tunnel local awarding ports from the client to the server or vice versa through the SSH tunnel.
Create the User and Grouping
Next I will create a user and group they should exist locked to our web root folder as follow.
# addgroup sftp
# useradd -m -s /bin/false -Thousand sftp sftpuser01
The -m pick will create the user's abode directory and the -s option volition set up the user's shell to the folder path /bin/simulated and therefore will prevent the user from accessing the beat out.
-Yard will add our sftpuser01 to our previously created sftp group.
We as well have to set a password for the sftpuser01 by executing
# passwd sftpuser01
In club to add yet existing user's to the sftp group, you tin add them as follows
# usermod -G sftp user123
# usermod -south /bin/faux user123
To determine in which groups a user is, yous can use the following control
# groups sftpuser01
To list members of a group use
# getent group sftp
Adjust permissions for the Abode Directory
We need to make the root user as owner for the abode directory in order our user's will be able to login to.
# chown root:root /home/sftpuser01
# chmod 0755 /home/sftpuser01
We will also create a new binder in the user's home directory where information technology can upload, download and edit files for. Further we will set this user as owner for the directory and the group volition exist www-data, in which the user also named world wide web-data is member and is running the apache2 webserver in Ubuntu.
# mkdir /home/sftpuser01/web
# chown sftpuser01:world wide web-data /home/sftpuser01/webYou can decide the user which is running the apache2 webserver with the following commands:
# ps aux | egrep '(apache|httpd)'
or
# apachectl -S
From now on the user is able to access its folder but without the pick to break out from its abode directory.
Mountain Web Root Directory to the Habitation Directory from the User
Every bit we want to enable the user to upload, download and edit files within our spider web root directory, we finally demand to mount that spider web root directory to the user's previously created home directory and here to the created web folder.
In order that the user will exist able to edit existing files and folders inside the mounted web root directory, we volition execute the chown command once again and this time recursive.
# # mount --bind /var/world wide web/website /home/sftpuser01/web # # chown -R sftpuser01:www-data /dwelling/sftpuser01/web
We will also ensure that new files and folders created in our binder web will inherit its grouping ID(setgid), rather than the primary grouping ID of the user who created the file, and therefore volition set every bit owner the sftpuser01 and the group www-information by using the chmod g+s control.
# # chmod thousand+south /home/sftpuser01/web To remove the inheritance y'all have to execute the following command btw. # chmod g-south /dwelling/sftpuser01/web The aforementioned for the user ID (setuid) !!!!! can exist configured on FreeBSD, other UNIX & Linux systems just ignore u+s !!! # chmod u+southward file
In case the spider web server apache2 needs to be able to write into some folders, y'all can let write access to these folders for apache2 as follows.
# chmod g+w /dwelling/sftpuser01/web/<Folder to exist writeable>
Farther that the mount volition still exist after a reboot, we also add it to the /etc/fstab file.
# /var/www/website /home/sftpuser01/spider web none demark 0 0
Troubleshooting
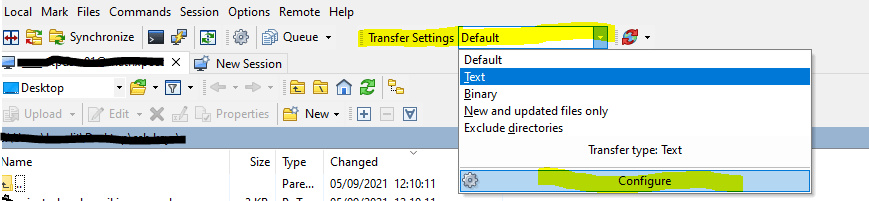
If y'all run into the following mistake by trying to modify files with WinSCP.
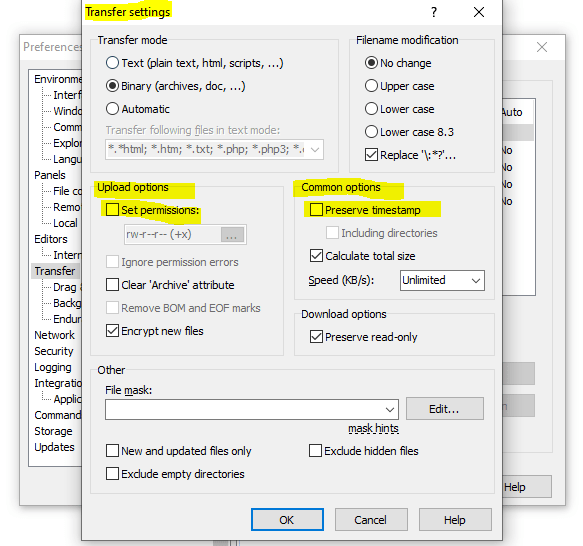
Upload of file .. was successful, but error occurred while setting the permissions and/or timestamp. If the problem persists, turn off setting permissions or preserving timestamp. Alternatively you lot tin plow on 'Ignore permission errors' pick.
- On some systems (due east.g. Linux), you lot demand to be an owner of the file (write permissions are not plenty) to modify its permissions or timestamp (yous volition encounter an mistake like"Permissions denied" in error details).
- Some servers practise not support updating file timestamp or permissions at all (y'all will come across an error like"The server does not support the operation" in mistake details).
- Some servers are set up to pickup any uploaded file immediately, process information technology somehow and delete or move it away. If the server is quick enough, it does that before WinSCP is able to update the file timestamp or permissions (you lot will run across an fault like"No such file or directory" in mistake details).
Links
abercrombiebeirt1990.blogspot.com
Source: https://blog.matrixpost.net/set-up-a-sftp-chroot-jail/
0 Response to "Upload of File Was Successful but Error Occurred While Setting the Permissions and/or Timestamp"
Post a Comment